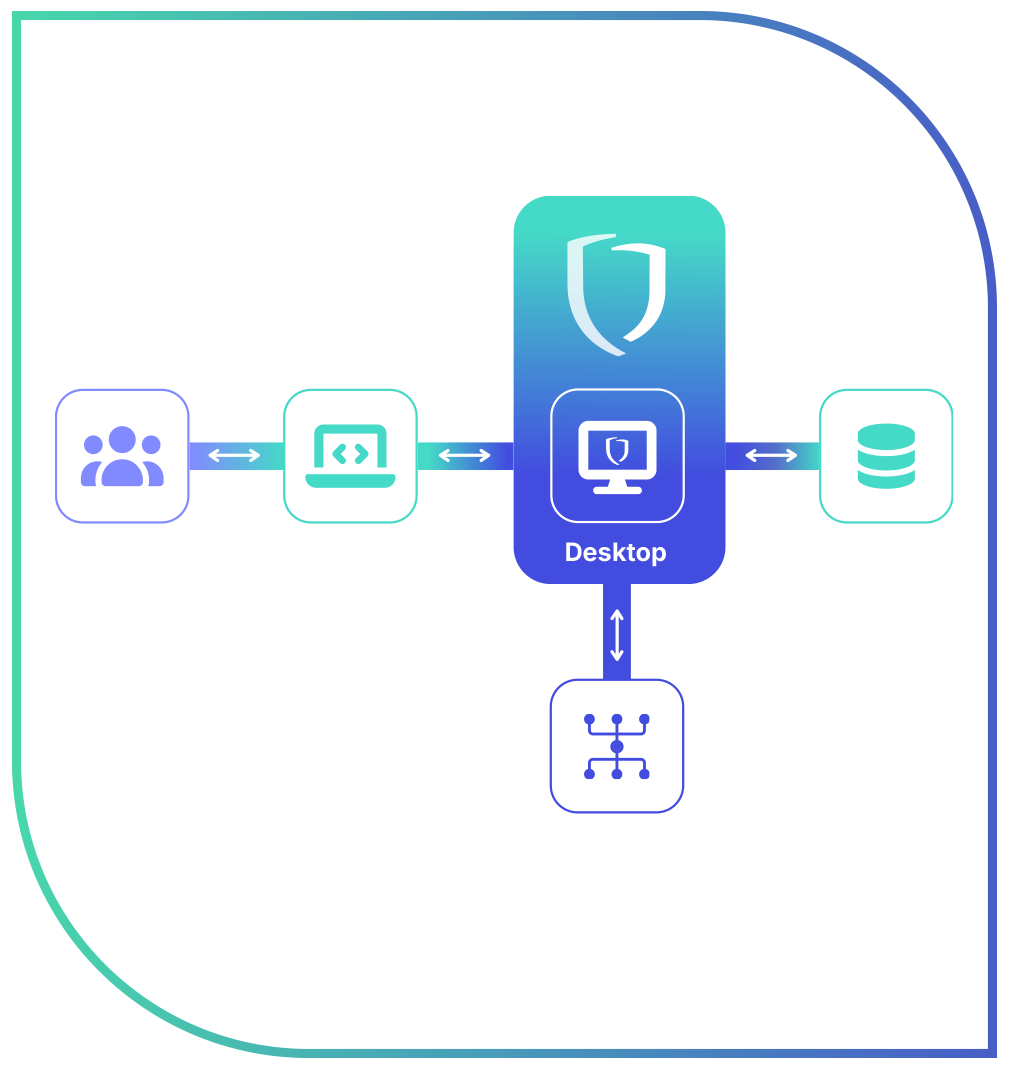
Serves as a secure intermediary
By containing all activity within a shielded environment, it prevents any lateral movement, data leakage, or unauthorized interaction with critical systems.
Users' endpoints never connect directly to sensitive systems.
All activity is logged, audited, video-recorded, and controlled.
Drastically reduces the risk of user's endpoint vulnerabilites propagating to critical systems.
Simplified and practical Zero Trust approach with minimized attack surface by design.
PRIVILEGED ACCESS MANAGEMENT
AND MUCH MORE
Endurance provides a Remote Shielded Workspace (RSW) that functions as an air-gapped layer between user endpoints and critical IT/OT assets — breaking the protocol.
Combining PAM functionalities, within a defense-in-depth (DiD) architecture, and a fully shielded environment at every level – from desktop to applications
Endurance is a next-generation solution that acts as an enclave, controlling access to critical assets while ensuring the protection of sensitive information — at rest, in transit, and in use.
KEY FEATURES INCLUDE
ENDURANCE is the perfect ally for organizations that must comply with the Directive (EU) 2022/2555 (NIS2), or recommendations such as ISO 27001/2 and ENS.
HOW IT WORKS

Protected Assets
Active Users
Of Availability
WE HELP YOU
If you need to learn more about our solutions and wish to obtain technical or commercial information, please fill out the following form:
Contact form










