Cosmikal Awarded the CCN-CERT 2025 CPSTIC Award in the SME Category
27 de November de 2025
What is cyber risk and why your company cannot ignore it
11 de December de 2025The Need for Comprehensive Cybersecurity Solutions in 2026
In 2025, cybersecurity solutions are no longer isolated tools. Today, the complexity of business environments, combining on-premises, cloud, OT, IoT, and hybrid infrastructures, has transformed cybersecurity into a comprehensive and adaptive ecosystem. Therefore, it is no longer just about preventing attacks, but also ensuring operational continuity, resilience, regulatory compliance, and the trust of customers and partners.
The global and local context reinforces this need:
- Cost of data breaches: In 2024, the global average cost of a breach reached USD 4.88 million.
- Cloud incidents: 61% of organizations experienced at least one cloud security incident in the past 12 months, a significant increase from previous years.
- Ransomware in Spain: Growth exceeded 116%, rising from 62 incidents in 2024 to 134 in 2025.
- Threats to SMEs: Historically less protected, they have become strategic targets for cybercriminals.
- Advanced attacks: Criminals’ use of artificial intelligence enables hyper-personalized phishing, lateral movement, exploitation of unpatched vulnerabilities, and supply chain attacks.
At the same time, regulatory pressure is increasing. Standards such as NIS2, DORA, GDPR, ISO27001, and sector specific regulations require organizations to maintain control, traceability, and resilience. As a result, cybersecurity is no longer an optional expenditure but a strategic asset.
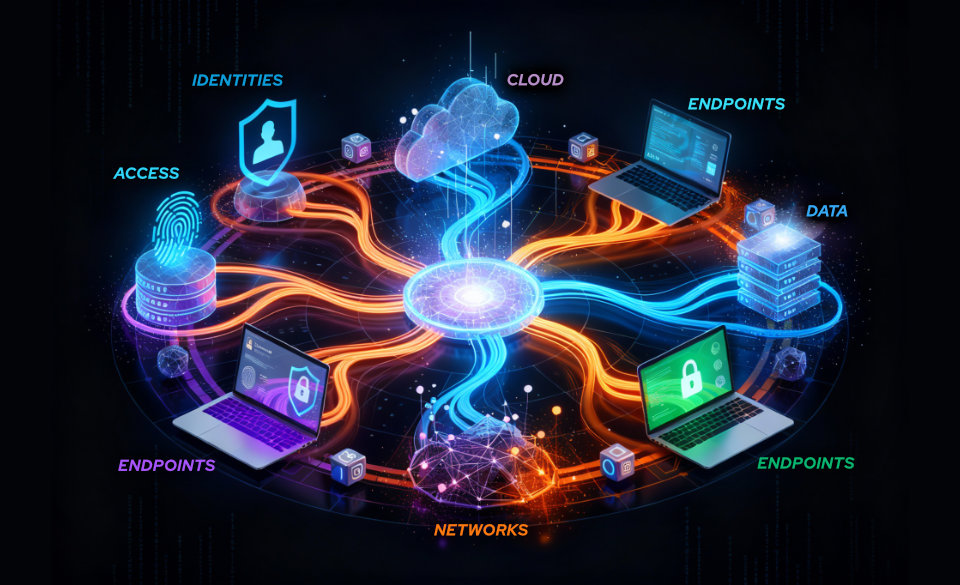
In 2026, an effective security architecture can not rely on disconnected solutions. Instead, it must be designed as aliving ecosystem, where identities, access, data, networks, endpoints, and cloud environments are managed in an integrated and adaptive manner against emerging threats.
This article outlines the 10 fundamental taxonomies that enable organizations to build a robust, scalable, and future-ready corporate security architecture.
1. Identity & Access Management (IAM)
IAM forms the foundation of modern security. It manages who accesses what, when, and how covering human users, machine identities, APIs, service accounts, and applications. Today’s complexity demands solutions supporting hybrid environments, cloud, directory federation, adaptive MFA, passwordless authentication, SSO, and access governance policies.
Modern IAM includes automated provisioning, onboarding/offboarding, segregation of duties (SoD), and periodic access reviews, ensuring regulatory compliance. It also provides full traceability for audits and forensic investigations.
Key points
- Unified identity management across hybrid environments (on-prem + cloud).
- Strong authentication: adaptive MFA and passwordless.
- Permission governance and historical traceability.
2. Privileged Access Management (PAM)
PAM governs high-privilege identities, which represent the greatest risk within any organization. Advanced PAM combines secure credential vaulting, granular access control, session brokering, and activity recording to protect critical systems.
It also enables just-in-time (JIT) privileges, automatic access revocation, segregation of duties, and complete session recording. This ensures that privileged users operate securely without compromising compliance or operational resilience.
Key points
- Encrypted vault for critical credentials.
- Temporary privilege assignment and granular control.
- Secure session brokering and full session auditing.
3. Data Loss Prevention (DLP)
DLP protects critical data by detecting, controlling, and preventing accidental or malicious leaks. It uses advanced techniques such as fingerprinting, semantic analysis, OCR, and contextual evaluation, applying policies based on roles, data type, channel, risk, or location.
It integrates control over USB, email, printing, APIs, cloud, and SaaS, preventing exfiltration, ensuring compliance, and minimizing risks without disrupting daily operations.
Key points
- Automatic classification of sensitive data and content analysis.
- Context-based policies for data in use, in transit, and at rest.
- Blocking and monitoring of leaks: USB, email, cloud, downloads.
4. Virtual desktop infrastructure (VDI)
VDI and isolated desktops eliminate dependency on insecure endpoints by centralizing applications, data, and policies. Users access “thin” terminals that do not store critical information, preventing local persistence of data and credentials.
This approach supports centralized updates, policy governance, IAM, PAM, and DLP integration, significantly reducing the attack surface in distributed, remote, or hybrid environments.
Key points
- Centralized, isolated remote desktop environments.
- Centralized management of images, software, and policies.
- Minimized attack surface: endpoints do not store critical data.
5. Defense in Depth (DiD)
DiD implements multiple protection layers so that the failure of one layer does not compromise the entire system. This strategy combines network segmentation, access control, endpoint hardening, monitoring, and auditing to ensure resilience against complex attacks.
Key points
- Network segmentation and micro-segmentation.
- Access control, endpoint hardening, and least privilege.
- Continuous monitoring, logging, and coordinated response.
6. Endpoint / Workload Protection: EDR / XDR
Endpoints and workloads remain primary attack vectors. EDR detects advanced threats by analyzing behavior, memory, processes, and lateral movement. XDR expands visibility to network, identity, cloud, and logs, enabling unified detection and response to multivector attacks.
Automation and immediate containment allow incidents to be mitigated before they materialize, ensuring operational continuity even in critical environments.
Key points
- Advanced threat detection on endpoints and workloads.
- Multilayer telemetry correlation (XDR).
- Automatic containment, quarantine, and remediation.
7. Next-Generation Firewall (NGFW) + Segmentation / Zero Trust
Modern NGFWs inspect traffic up to the application layer (Layer 7), including TLS/SSL, user, and context. Combined with Zero Trust, they enable granular control, network segmentation, and isolation of critical zones. Integration with IAM, PAM, and SASE strengthens multilayer security architectures.
Key points
- Deep inspection (Layer 7) and user/application-based control.
- Network segmentation and micro-segmentation.
- Integration with Zero Trust and adaptive policies.
8. SIEM + UEBA
SIEM centralizes logs and events from all corporate systems, providing visibility and traceability. UEBA adds behavioral analysis of users and entities, enabling early detection of insider threats, privilege abuse, or lateral movement.
Key points
- Collection and normalization of corporate events.
- Real-time correlation, alerts, and forensic analysis.
- Anomaly detection for users and entities (UEBA).
9. SASE + ZTNA
SASE + ZTNA redefines corporate access: entry is no longer granted to the entire network but only to specific resources, based on identity, context, risk, and device posture. This reduces the attack surface, enforces least privilege, and adapts natively to cloud and edge.
Key points
- Access based on identity, context, and risk.
- Distributed, adaptive security, cloud/edge-native.
- Minimum necessary access to critical resources.
10. CASB
CASB ensures security, visibility, and governance across cloud and SaaS environments. It enables detection of shadow IT, control over access and use of external apps, protection of sensitive data through encryption, DLP, or tokenization, and continuous compliance and auditing.
Key points
- Detection and control of cloud services (shadow IT).
- Data protection: encryption, DLP, tokenization.
- Auditing, roles, session control, regulatory compliance.
Conclusion: A New Security Model for the Business World
Cybersecurity solutions can no longer be understood as a catalog of independent tools, but as a central nervous system connecting identity, access, data, network, endpoint, cloud, and operations.
Digital transformation has created a business infrastructure that is more flexible, distributed, and efficient, yet more exposed than ever.
Consequently, every remote connection, API, cloud service, and IoT device is a potential entry point that must be governed, monitored, authenticated, and protected.
The most resilient organizations in 2026 will not necessarily be the ones that spend the most on cybersecurity. They will be the ones capable of integrating critical taxonomies into a common framework based on Zero Trust, intelligent automation, continuous observability, and coordinated responses. The value lies not in buying tools but in ensuring that identity, access, data, network, and operations function as a cohesive ecosystem.
Technology Governance
IAM and PAM ensure that only the right identities perform the proper actions. DLP protects the most valuable asset: information. VDI and secure remote access reduce the attack surface. DiD provides layered architecture that mitigates failures.
EDR/XDR expand visibility and response capabilities. NGFW, segmentation, and Zero Trust eliminate lateral movement. SIEM + UEBA provide the organization’s “analytical brain.”
SASE and ZTNA bring security to where users are. CASB governs the chaos of the modern cloud.
Together, these elements allow any organization industrial, financial, healthcare, energy, educational, or technological to move toward a predictive, contextual, and automated security model. This enables them to operate in an environment where risk is constant, attackers use AI, and systems evolve rapidly.
Ultimately, security in 2026 and beyond will be, above all, a discipline of technological governance. This means protection must cover identity to application, endpoint to cloud, and network to operations. Decisions will be based on data, context, and continuous analysis. Organizations adopting this model will reduce risk while becoming more competitive, efficient, and trustworthy.
Cosmikal Solutions, an integration pillar
Cosmikal’s Endurance and Ranger solutions enable integration of multiple taxonomies into a corporate ecosystem:
- Endurance: A hardened remote work environment integrating IAM, PAM, VDI, DLP, DiD, and Zero Trust, encrypted vaulting, session brokering, auditing, and full endpoint isolation.
- Ranger: A hardened local work environment using thin clients and non-persistent desktops, covering secure endpoints, hardening, access control, and segmentation to reduce data leak risks and system exposure.
Both solutions embody the modern cybersecurity strategy for 2026, integrating identity, access, data, endpoints, network, monitoring, and secure access with full traceability, regulatory compliance, and operational resilience. They form the foundation of an architecture prepared for the threats of 2026 and beyond.
They are the foundation of an architecture prepared for the threats of 2026 and beyond.